Mirai and the attacks against Lonestar Cell (Liberia)

From the 31st of October, we have been monitoring a series of attacks targeting infrastructure of Lonestar Cell, a GSM operator in Liberia.
Spoofit has been monitoring Mirai from the very first early attacks and to our knowledge we were the first ones publicly documenting the communication protocols even before the Mirai’s code was publicly released by Anna-Sempai in Hack Forums. There has been some speculation about the real impact of these attacks and the motivations of the attackers. These are our findings!
We can confirm that one of the command and control (C2) that we are monitoring did launch the attacks against the following destinations the 31st of October.
- 41.57.81.0/24 (Lonestar. Liberia)
- 41.57.81.30 (Lonestar. Liberia)
During the 2nd of November, a few rounds of attacks included.
- 41.181.245.182/32 – MTN Routing
- 41.181.245.186/32 – MTN Routing
- 41.181.190.196/32 – MTN Routing
- 41.181.245.251/32 – MTN Routing
- 41.181.189.244/32 – MTNBS-CUST-41-181-176-0-20
The 4th and 5th of November, the very same botnet launched attacks against these targets:
- 41.181.189.69/32 – MTNBS-CUST-41-181-176-0-20
- 195.50.122.182/32 – Customer Serial Link LEVEL3 Europe IP
- 41.181.189.244/32 – MTNBS-CUST-41-181-176-0-20
- 41.181.247.77/32 – MTNBS-CUST-41-181-244-0-22
- 213.207.191.70/32 – MTN_Cyprus_Limited
The 6th of November, a new network prefix was added to the attacks.
- 168.253.25.75/32 – Novafone
- 41.181.189.244/32 – MTNBS-CUST-41-181-176-0-20
The 8th of November, the attacks continue targeting
- 168.253.26.254/32 Novafone
- 168.253.27.254/32 Novafone
- 41.181.189.245/32 MTN
The 9th of November, the attacks continue targeting
- 168.253.27.75/32 Novafone
- 41.57.81.19/32 Lonestar
Lonestar Cell and DDOS
If we review the targets we recorded from the 2nd to the 4th of November, we can see that the attackers are targeting the prefix 41.57.81.0/24. Only one attack was launched against smtp1.lonestarcell.com (41.181.87.0/24) the 31st of October 2016.
Lonestar targets (31 Oct – 4 Nov)
# Attacks , Target, Type 26 , 41.57.81.27/32 , ACK 16 , 41.57.81.30/32 , ACK 13 , 41.57.81.29/32 , ACK 12 , 41.57.81.25/32 , ACK 11 , 41.57.81.28/32 , ACK 11 , 41.57.81.26/32 , ACK 8 , 41.57.81.0/24 , GRE-IP 5 , 41.57.81.0/26 , ACK 5 , 41.57.81.0/24 , ACK 4 , 41.57.81.27/32 , GRE-IP 3 , 41.57.81.30/32 , UDP 3 , 41.57.81.1/32 , ACK 3 , 41.57.80.0/20 , ACK 2 , 41.57.81.30/32 , SYN 2 , 41.57.81.0/24 , SYN 1 , 41.57.81.0/26 , SYN 1 , 41.57.81.0/24 , GRE-ETH 1 , 41.57.80.0/20 , SYN
What is going on with prefix 41.57.81.0/24?
Monitoring BGP announcements, we can see that the prefix 41.57.81.0/24 has been already months ago under DDOS mitigation by NeuStar.
2016-09-28 - 2016-11-06: 19905 - 41.57.81.0/24 NeuStar
2016-09-23 - 2016-09-27: 16637 - 41.57.80.0/23 MTN
2016-09-16 - 2016-09-22: 19905 - 41.57.81.0/24 NeuStar
2016-08-17 - 2016-08-19: 16637 - 41.57.80.0/20 MTN
2016-01-07 - 2016-08-14: 16637 - 41.57.81.0/24 MTN
So, it seems that the attacks against Lonestar Cell are not new. Some information is available in a press release of the company (28?-29th October 2016) here
A new prefix is attacked
A new prefix was attacked the 6th of November, 168.253.25.0/24. This prefix also seemed to be affected by DDOS attacks before.
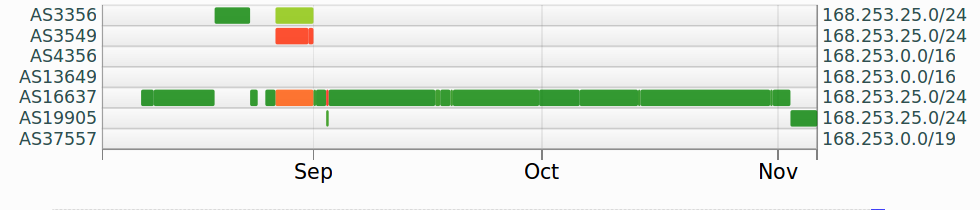
2016-11-02 - 2016-11-06: 19905 - 168.253.25.0/24 NeuStar
2016-08-31 - 2016-11-01: 16637 - 168.253.25.0/24 MTN
2016-08-26 - 2016-08-30: 3356 - 168.253.25.0/24 Level 3
2016-08-23 - 2016-08-25: 16637 - 168.253.25.0/24 MTN
2016-08-18 - 2016-08-22: 3356 - 168.253.25.0/24 Level 3
2016-08-09 - 2016-08-17: 16637 - 168.253.25.0/24 MTN
2016-01-01 - 2016-03-08: 37557 - 168.253.0.0/19 NOVAFONE-lr, LR
Judging by the BGP announcements, it seems to us that Denial of Service attacks against the operator are not new and have been present in their networks for the past three months at least.
Linking Gayfgt with Mirai Command and Controls
We have looked into the command and control that launched the attacks and there is overlap with other botnet families as Gayfgt command and control from middle September.
Attackers using VDOS-S against Lonestarcell
After reviewing the VDOS-S logs that leaked the past month, we have identified three accounts that targeted Lonestarcell. The accounts targeted specifically IPs of Lonestarcell and not anything else. We make a sample of the logs available here
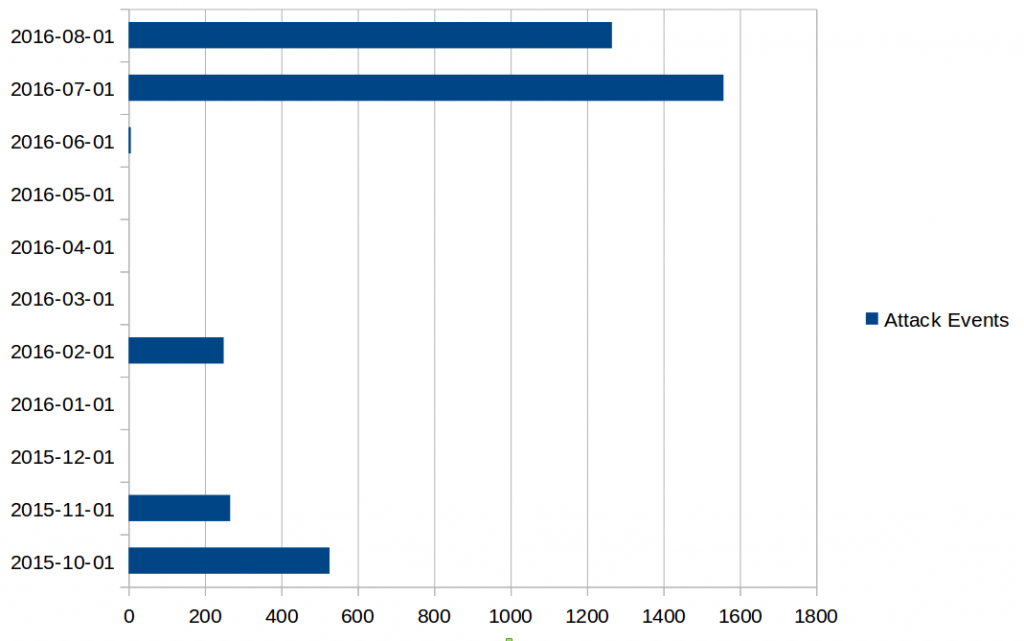
We also aggregated the number of attacks that VDOS-S launched against the operator and we could clearly see an increase of attacks starting July 2016.