The “Sindicate” and DNS amplification
Thanks to the leak of data from VDOS stress tester we could get access to the history of commands run in the server. A selection of those commands shows how the owners of VDOS where feeding their attack amplification tools with lists of open resolvers.
The lists were obtained by actively scanning the whole Internet from a server of an organization known as the “Sindicate Group”. This is the story of how we found about the “Sindicate Group” and their network mobility.
How DNS amplification works?
In a nutshell, a DNS amplification attack works as follows: the attacker sends a DNS request against a set of open resolvers. The requests contain the victim IP address as source, the source address is spoofed.
The DNS request will result in a large response from the open resolvers that is sent back to the victim, flooding it with large volumes of traffic.
With this type of attack, the attacker normally needs 1/40th of the bandwidth. Yes, as a rule of the thumb: 1 Gbps of spoofed bandwidth results in 40 Gbps at the victim’s size.
So what does the attacker need to perform the attack?
– The ability of sending spoofed UDP traffic (Spoof IT!)
– A large list of open resolvers with good and stable bandwidth (the “fresh list”)
– A good DNS query that will return a large DNS answer. i.e. An authoritative DNS server that has large DNS records.
Once the attacker has found a hosting provider that allows traffic to be spoofed (in the case of VDOS, Verdina). The attacker needs to scan the Internet for open resolvers.
The attacker can then opt for using an existing domain name with large responses (normally some .gov domain) or setup its own miss-configured DNS server.
So let us go back now to the commands that VDOS run in their servers. We can see that they are fetching lists of open resolvers from four locations.
curl 185.130.5.209/dns.txt | shuf > dns_amp2.txt
curl 185.130.5.209/dns.txt | shuf > dns_amp.txt
curl 185.130.5.209/finaldns.txt | shuf > dns_amp.txt
curl https://vdos-s.com/
killall screen; rm -rf dns_amp.txt;curl 93.174.95.38/finaldns.txt | shuf > dns_amp.txt
killall screen;rm -rf dns_amp.txt;curl 93.174.95.38/finaldns.txt | shuf > dns_amp.txt
killall screen;rm -rf dns_amp.txt;curl http://104.238.181.185//finaldns.txt | shuf > dns_amp.txt
killall screen;rm -rf dns_amp.txt;curl http://104.238.181.185/finaldns.txt | shuf > dns_amp.txt
killall screen;rm -rf dns_amp.txt; curl http://93.174.95.38/finaldns.txt | shuf > dns_amp.txt
rm -rf dns_amp.txt;curl 185.130.5.209/finaldns.txt | shuf > dns_amp.txt
rm -rf dns_amp.txt;curl http://82.118.233.7/dns_amp.txt | shuf > dns_amp.txt
rm -rf dns_amp.txt;killall screen;curl 93.174.95.38/finaldns.txt | shuf > dns_amp.txt
rm -rf portmap.txt;curl 93.174.95.38/portmap.txt | shuf > portmap.txt
LT, Latvia |AS203569 Sindicate Group Ltd |185.130.5.209| NL, Netherlands| AS29073 Ecatel Network|93.174.95.38| US, USA | AS20473 Choopa LLC |104.238.181.185| BG, Bulgaria| AS200002 Kandi EOOD|82.118.233.7|
So What is so special about these four locations? That from those locations is allowed to scan the whole Internet for open resolvers.
The “Sindicate Group”
Since late 2015, we have been monitoring the scanning of open resolvers from IP addresses of the “Sindicate Group”. The IP address 185.130.5.209 is present in many of our honeypots placing requests for the following domains:
amplists.com access-board.gov cpsc.gov ic3.gov
The infamous amplists.com
Let us now look into one of the domains involved in the DNS amplification. VDOS is using servers from the Sindicate Group to build lists of DNS open resolvers reaching to the domain amplists.com
Who hosts the amplists.com DNS AMP Domain?
The domain name server ns1.amplists.com was hosted at Quasi Networks LTD,
formerly known as Ecatel. By the way, Ecatel/Quasi has changed name again to Novogara.
route: 89.248.160.0/21 descr: Quasi Networks LTD (IBC) origin: AS29073 mntby: QUASINETWORKSMNT created: 20060714T16:36:01Z lastmodified: 20151109T12:02:24Z source: RIPE
Until late September 2016, The Sindicate Group operated the prefix the IP range 185.130.4.0 – 185.130.7.255 allocated in December 2015. The Sindicate was also a LIR with address Didlaukio st., 59-205, Vilnius, LITHUANIA. The “person” behind those resources is Antonio Jordan with this details:
person: ANTONIO JORDAN org: ORG-OEN1-RIPE abuse-mailbox: abuse@ovh-eu.net address: Commonwealth of Dominica address: 3rd Floor, C&H Towers, Comer of Great Marlborough and Great George Streets address: Roseau, 00152 phone: +17674482899 nic-hdl: PB19075-RIPE mnt-by: pin-dx created: 2015-12-01T15:17:16Z last-modified: 2015-12-12T17:51:52Z source: RIPE
The “Sindicate” and the other offshore hostings
Two autonomous systems were very active during the first six months of 2016 in the heavy scanning:
– AS203569 known as SILKAS Sindicate Group Ltd, LT with company in Dominica. Also operating as OHS4YOU_DC. offshore.la with address in Didlaukio st., 59205, 08302 Vilnius LITHUANIA +37062272170. sindicategrourp@gmail.com
– and, AS203734 known as HOSTSHIELD
Mobility is key
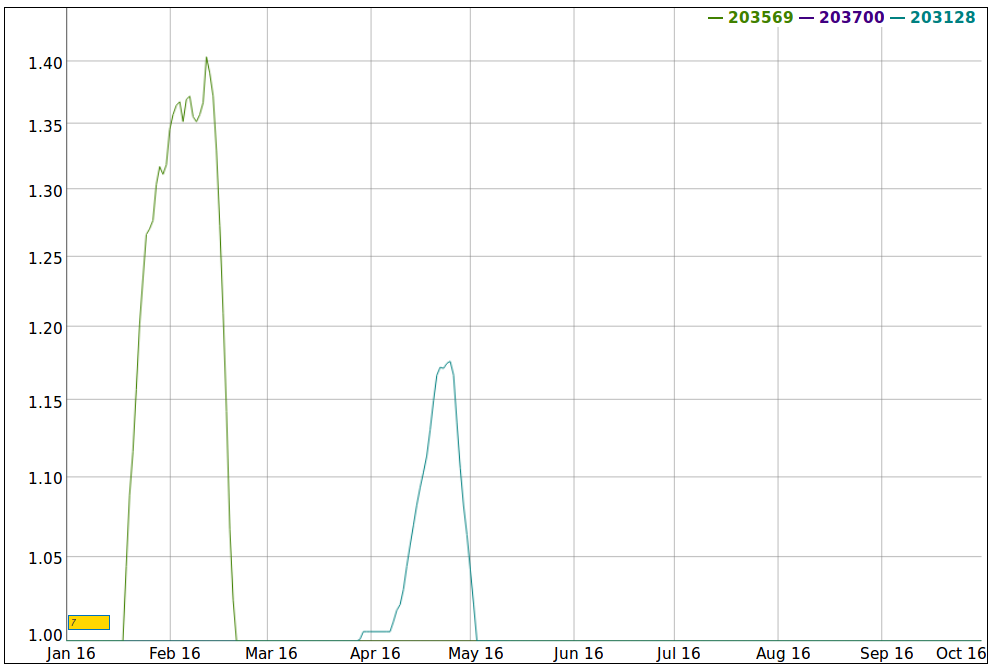
Tracking the quick movements of the Sindicate Group has been inspiring at least.The prefix has been announced by half a dozen of Autonomous Systems in the last six months and multiple upstream providers. It is our understanding that the Sindicate Group operates 2-3 months maximum per location, when enough abuse complains arrive, the move to another sympathetic location with new upstreams and ASN.
During their peak of activity, Sindi Host Subdivision or Sindicate Group Ltd used the AS203700 and also got their prefixes announced by their upstream provider AS61272 INFORMACINES SISTEMOS UAB (Lithuania). Finally the Sindicate moved to ASN AS203128.
Later on, The Sindicate’s ASN: AS203569 and prefix 185.130.5.0/24 were moved to AS60117 with Nforce Entertainment (AS43350) in Amsterdam as upstreams.
List of ASNs and registration dates
2016-03-24 AS203128 Sindicate Group Ltd 2015-12-09 AS203569 Sindicate Group Ltd 2015-11-16 AS203700 Sindicate Group Ltd
(Yes! Host Sailor is another interesting location that will deserve its own chapter in Spoof IT!).
So how VDOS got access to those scanning servers?
All seems to point to a few bulletproof hosters associated with the domain names: skylakegroup.biz, hqserver.net, maxidedcom, service.hqserver.net and hostshield.net.
So our best guess is that VDOS rented servers from MaxiDED Ltd as part of their stress tester-building infrastructure.
MaxiDed Ltd.(2015/IBC18382) Type: Company Status: Registered Principal Place of Business: 3rd Floor, C&H Towers, Corner of Great Marlborough and Great George Streets, Roseau, DOMINICA Date of Registration: January 19, 2015 Registry: Dominica (CIPO) Sindicate Group Ltd. (2015/IBC18876) Type: Company Status: Registered Principal Place of Business: 3rd Floor, C&H Towers, Corner of Great Marlborough and Great George Streets, Roseau, DOMINICA Date of Registration: November 9, 2015 Registry: Dominica (CIPO)
Let us move it, move it!
The “Sindicate Group” keeps moving, back in August 2015 they merged back their /22 prefix in AS48031, infamous a few years ago for the Browlock ransomware
Here is a list of their where abouts in the last months.
Mobility of 185.130.6.0/24
2016-08-12 - 2016-09-29: 48031 - 185.130.4.0/22
2016-07-13: XSERVER-IP-NETWORK-AS , UA
2016-05-15 - 2016-08-07: 200039 - 185.130.6.0/24
2016-07-13: HYDRACOM-AS , GB
2016-04-16: HYDRACOM-AS Hydra Communications Ltd, GB
2016-03-29 - 2016-04-26: 203128 - 185.130.6.0/24
2016-04-08: MAXNET , MD
Mobility of 185.130.5.0/24
2016-08-12 - 2016-09-29: 48031 - 185.130.4.0/22
2016-07-13: XSERVER-IP-NETWORK-AS , UA
2016-07-14 - 2016-08-10: 31863 - 185.130.5.0/24
2016-04-08: DACEN-2 - Centrilogic, Inc., US
2016-03-29 - 2016-05-16: 23456 - 185.130.5.0/24
2016-04-08: -Reserved AS-, ZZ
2014-03-29: -Reserved AS-,ZZ
2016-02-15 - 2016-03-28: 60117 - 185.130.5.0/24
2014-05-15: HS Host Sailor Ltd.,AE
2016-01-01 - 2016-02-14: 203569 - 185.130.5.0/24
2015-12-11: SILK-AS Sindicate Group Ltd,LT
The Sindicate group has used the following ASNs: AS203569 and AS203128.
In th next chapter of this sequel we will talk about AS203466 and the connection of this ASN with VDOS and the Sindicate Group.